Identity Provider – Common use cases
Identity Provider (IdP), is a service that implements OpenId Connect (OIDC) and SAML2 identification standards, which identifies users, enabling them to access systems and applications. The IdP can be used to implement single sign-on (Single Sign On - SSO), which allows the user to access all the applications included in the scope of identification based on a single identification event without separate identification. IdP connects to identification methods as needed. WeAre has implemented an authentication proxy service model that relies on existing OIDC authentication sources (e.g. Azure AD, Google, Facebook, etc.). User data produced by identification methods can be enriched from other sources, such as the organisation's IdM system. IdP is implemented with the open source Shibboleth Identity Provider software.
Enrichment of identification
It is possible to implement phases to the identification process, in which the user identification information obtained from the identification method is enriched with user data from external sources. For example, if a customer's user authentication is based on the Azure AD authentication service, but the user role information is stored in a separate system, the role information can be retrieved from another system (e.g., CRM) after the actual authentication event and then added to the authentication response. The decision on user access to the application can be made based on the role information.
The enrichment of authentication information in connection with an authentication event saves the implementation of a separate synchronisation to the service, as the user role is handed over during the authentication event.
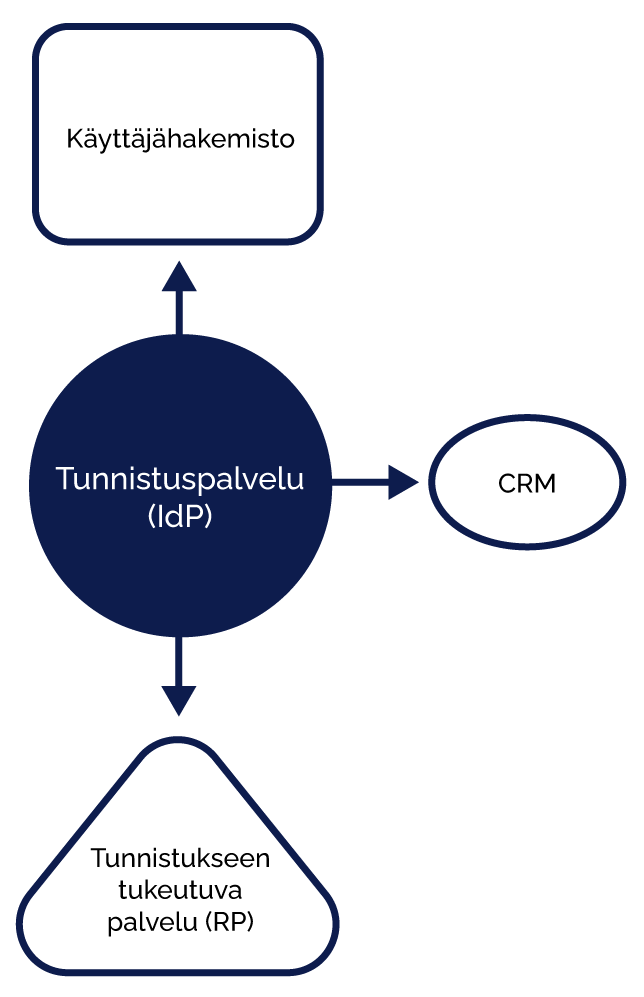
Identification adapter
The customer may have an identity provider service in use, which is not compatible with a system in use, that relies on authentication. Typically, the client has a SAML2 authentication solution, but the service has implementations for only OIDC-based access control. Or the case may be the other way around.
The authentication service can act as an adapter, i.e. an intermediary, where the authentication method is adapted to the service in the form for which it has ready-made solutions. Even the very unique and hand-tailored services can often be protected by authentication, even if they were not initially implemented with a single sign-on method or with connections to modern authentication protocols.

DO YOU WANT TO
HEAR MORE?
Contact us

JUHA AHLGREN
Sales and Marketing
juha.ahlgren@weare.fi
+358 44 504 4828

